|
The House Judiciary Committee today announced its long-awaited bill that reauthorizes Section 702 of the Foreign Intelligence Surveillance Act (FISA) while reforming provisions that have allowed warrantless spying on Americans by federal agencies.
Enacted in 2008, Section 702 permits the FBI, the CIA, the National Security Agency, and the National Counter Terrorism Center to search through billions of warrantlessly acquired international communications to surveil foreign targets on foreign soil. The emails, texts messages, internet data, and other communications of Americans are also incidentally swept up in this program, allowing agencies to look for specific information about U.S. persons (U.S. citizens and permanent residents) without a warrant, as required by the Fourth Amendment of the U.S. Constitution. Statement of Bob Goodlatte, former Chairman of the House Judiciary Committee and PPSA Senior Policy Advisor: “The House Judiciary Committee has unveiled the most important government surveillance reform measure since the creation of FISA in 1979. “This bill addresses a growing crisis. Our government, with the FBI in the lead, has come to treat Section 702 – enacted by Congress for the surveillance of foreigners on foreign soil – as a domestic surveillance program of Americans. “The government used this authority to conduct over 200,000 ‘backdoor searches’ of Americans in 2022. Section 702 has been used to search the communications of sitting House and Senate Members, protesters across the ideological spectrum, 19,000 donors to a congressional campaign, journalists, and a state court judge. The American people can see that Section 702 has morphed into something that Congress never intended. “The House Judiciary Committee – with the leadership of Chairman Jim Jordan, Ranking Member Jerry Nadler, and Rep. Andy Biggs – has now crafted a bill that restores the rule of law. This bill allows Section 702 to continue to protect Americans by conducting surveillance of foreign spies and terrorists. But it does so in a way that respects the Fourth Amendment. By achieving this balance, the Judiciary Committee’s bill promises to rebuild the trust of the American people in the law, strengthening freedom from unwarranted surveillance and our right to privacy, as well as our national security.” Statement of Gene Schaerr, PPSA general counsel: “The House Judiciary Committee bill brings sweeping and needed reforms to Section 702 while respecting the legitimate needs of national security. It addresses the prime problems with this authority, establishing a clear warrant requirement. But it also includes some masterful reforms to practices and programs outside of Section 702 that, if left unaddressed, would merely be used by government agencies to end-run the Section 702 reforms. “The House Judiciary Committee bill, for example, imposes a warrant requirement on the government to access and inspect data scraped from consumer apps and sold to the government by data brokers. Without this fix, the government would continue to have ready access to Americans’ most sensitive information – about our medical issues, our location histories and travels, our financial records, and those with whom we associate for political, religious, or personal reasons. “This bill also puts an amicus, a representative of the public’s interest in privacy, into the secret FISA courtroom to challenge the issuance of warrants when the government exceeds its authority. “For years, champions of the Constitution have had to play a game of whack-a-mole with the surveillance state, closing one surveillance loophole only to find federal agencies easily replacing it by exploiting another. Although it will likely see further improvements in the legislative process, the House Judiciary Committee bill closes most of the big loopholes, forcing federal agencies to respect the Fourth Amendment. “We commend Chairman Jordan, Ranking Member Nadler, and Rep. Biggs for their hard work and wise judgments in crafting a bill that will better protect both our national security and our constitutional rights.” Defenders of the surveillance status quo in Congress are perplexed by the success of reform proposals and are flailing in response. Some have made national media appearances that give the American people an inaccurate picture of how Section 702 works and how the government uses it to access large amounts of Americans’ personal information without a warrant.
One such champion did not do his cause any favors when he made inflammatory statements on Face the Nation on Sunday about the leading Members of Congress who want to bring Section 702 of the Foreign Intelligence Surveillance Act in line with the Fourth Amendment of the Constitution. We were told that Chairman Jim Jordan and many of his bipartisan colleagues on the House Judiciary Committee want to “hinder” the process of foreign intelligence and “don’t fully understand” Section 702’s “value and importance to national security.” Moreover, Jordan and his colleagues would “foolishly” cut off one of the most important tools for protecting national security. What we didn’t hear was anything about Section 702’s long litany of abuses, or the need to protect the freedoms and privacy of law-abiding Americans from government snooping. Protecting Americans’ rights and upholding the Constitution is a duty of the House Judiciary Committee. With primary jurisdiction over this program, the bipartisan team of reformers on the House Judiciary Committee understand this surveillance program all too well. They are working on a bill that has far greater substance than what Sen. Mike Lee has called the “window dressing” reforms of the House Intelligence Committee bill, the full text of which has yet to be released. It was never explained in this Face the Nation interview that Section 702 – enacted by Congress to authorize surveillance of foreign spies and terrorists on foreign soil – has morphed into a domestic spying program that in recent years has compromised the privacy of Americans millions of times. Add to that the practice of federal agencies buying Americans’ most sensitive and personal information from data brokers and holding and examining it without a warrant, as required by the Constitution, and you have a recipe for a surveillance state. Champions of surveillance are also wrong when they say that the bipartisan team that wants to reform Section 702 are hindering its passage. The bipartisan Judiciary Committee bill will reauthorize Section 702 for the purpose Congress intended – gathering intelligence about noncitizens outside the United States – while imposing a warrant requirement when the government wants to search Section 702-gathered information about American citizens. The Judiciary Committee, with a long history of protecting civil rights, is expected to soon mark up and pass a strong, bipartisan bill that will give federal agencies the tools they need to protect our national security while safeguarding our constitutional rights. Proposes GAO Investigation of CIA’s Section 702-Like Program As Congress debates reform of Section 702, Patrick Eddington, former CIA analyst turned Cato Institute senior fellow, offers a timely reminder of how much we don’t know about government surveillance of Americans.
In a piece in The Orange County Register, Eddington writes that for years prior to the 9/11 attacks, the CIA was “apparently conducting exactly the kind of internet ‘backbone’ surveillance now carried out under FISA Section 702 … with absolutely no judicial oversight.” Eddington notes that it took a lawsuit under the Freedom of Information Act against the Privacy and Civil Liberties Oversight Board (PCLOB) to reveal an audit by the Inspector General of the CIA that covered 1999-2000. The audit is heavily redacted. Despite the fact that millions of Americans live, work, and travel abroad, under the CIA’s Section 702-like program, the agency presumed a target was foreign when starting collection. The CIA only allegedly ended collection when it discovered the target was in fact an American. The CIA IG report admitted it “was unable to review every regulated activity.” Did other CIA collection activities ensnare the communications of Americans? Most important, Eddington writes that the redactions prevent us from knowing if this CIA program was terminated or if it still operating. What can be done? First, Eddington points to Rep. Nancy Mace (R-SC) and Jamie Raskin (D-MD), who last year tasked the Government Accountability Office to investigate the FBI’s use of “assessments” – de facto investigations that can be opened on any person or organization absent any criminal predicate. Eddington proposes Congress instruct GAO to expand its surveillance program inquiry to include the CIA’s surveillance program. A good place for the GAO to start would be to determine if this program is, in fact, still in operation. Second, Congress should look to the solutions of the Government Surveillance Reform Act to curb widespread abuses, including those in FISA’s Section 702, which also targets digital communications passing through the backbone of major telecommunications firms and internet service providers’ networks. The absence of sunlight is sure to provide a breeding ground for many abuses. A recent opinion-editorial in The Hill casts a harsh light on the unfolding state of “digital authoritarianism” in America’s schools. Public schools are increasingly adopting artificial intelligence to monitor students and shape curricula. This trend could ultimately have the effect of stifling education, invading privacy, and changing the attitude of adult American society about pervasive surveillance.
Civil rights attorney Clarence Okoh writes that “controversial, data-driven technologies are showing up in public schools nationwide at alarming rates.” These technologies include AI-enabled systems such as “facial recognition, predictive policing, geolocation tracking, student device monitoring and even aerial drones.” A report compiled by the Center for Democracy & Technology found that over 88 percent of schools use student device monitoring, 33 percent use facial recognition and 38 percent share student data with law enforcement. These surveillance technologies enable schools to punish students with greater frequency. A study conducted by Johns Hopkins University found that students at high schools with prominent security measures have lower math scores, are less likely to attend college, and are suspended more often compared to students in schools with less surveillance. The study claims to factor out social and economic background data. Okoh highlights a Florida case in which the sheriff’s office has purportedly used a secret predictive policing program against vulnerable schoolchildren. At some point, the punishments of “predictive” behavior could easily become a self-fulfilling prophecy. A group known as the People Against the Surveillance of Children and Overpolicing (PASCO) has found through litigation and open records requests that the Pasco, Florida, sheriff’s office has a secret youth database that contains the names of up to 18,000 children each academic year. According to PASCO, the sheriff’s office built this database using an algorithm that assessed confidential student records: everything from grades, attendance records, and histories of child abuse are used to assess a student’s risk of falling into “a life of crime.” Many programs directly target minority students. Wisconsin uses a dropout prevention algorithm that uses race as a risk factor. Such modeling, mixed with surveillance software in schools, could have a demonstrably harsher impact on minority students, leading to higher suspension rates. State legislators need to drill down into these reports and verify these claims. One avenue to explore is the role of parents in this process. Are they informed of these practices? Have they been sufficiently heard on them? We have sympathy for why some schools would feel the need to resort to such tactics. But if these facts pan out, then artificial intelligence has just opened up a new front – not just in the war on privacy, but one that could seal the fate of children’s future lives. It also could have an impact on adult society as well. An elementary school student might not understand what it means to be surveilled 24/7 and could become accustomed to it over time. This could lead to a generation of Americans who are inured to ever-present monitoring. If digital authoritarianism becomes the norm in school, it will soon become the norm in society. PPSA looks forward to further developments in this story. When Richard Nixon wanted his minions to run a super-secret surveillance operation that came to be known as the White House Plumbers, the president had it set up in Room 16 in the basement of the Executive Office Building. A recent White House memo obtained and reported by Wired shows that a massive dragnet surveillance program – warrantlessly scooping up phone records from Americans by the trillions – is now being run out of the White House today.
This program, currently called Data Analytical Services (DAS) allows federal, state, and local law enforcement to mine the details, though not the content, of Americans’ calls. As a study at Stanford University showed, metadata alone can reveal startling amounts of highly personal information. When the government adds “chain analysis” – moving outward from one target to the person he or she communicated with, and on to the next person – vast networks of associational groups, whether religious, political, or journalistic, can be X-rayed. “In response to a 2019 Freedom of Information Act request the Project for Privacy and Surveillance Accountability filed jointly with Demand Progress, we received a document from the Drug Enforcement Administration with a redaction into which one could easily fit the word ‘Hemisphere’” said Gene Schaerr, PPSA general counsel. “Hemisphere was the name of this warrantless surveillance program until it was rebranded as Data Analytical Services. Clearly, the government was holding on to something it didn’t want us to see. We had no idea, however, they were hiding it in the White House. With the ‘two-hop’ rule, government at all levels can not only target an individual, but also her spouse, children, parents, and friends. “This is nothing less than warrantless, dragnet surveillance at the national level,” Schaerr said. There is as of yet no evidence that implicates this program in political surveillance. But as with the Nixon Administration, running a program out of the White House has unique advantages. In the current era, a White House operation is not subject to the requirement to review its privacy impacts. It also cannot be subject to FOIA requests. Wired reports that the memo shows that over the years the White House has provided more than $6 million to target the records of any calls that cross AT&T’s infrastructure. Wired also reports that White House funding had intermittent starts and cancellations under the current and last two presidents. Still, the program seems to have been in continuous operation for over a decade. Internal records suggest that the government can access records held by AT&T for at least ten years. These records include the names of callers and recipients, the dates and times of their calls, and their location histories, although the 2018 Supreme Court opinion, Carpenter v. United States, established a warrant requirement for location data. On Sunday, Sen. Ron Wyden (D-OR) fired off a letter to Attorney General Merrick Garland saying, “I have serious concerns about the legality of this surveillance program, and the materials provided by the DOJ contain troubling information that would justifiably outrage many Americans and other Members of Congress.” This breaking news story is certain to provide more momentum for the Government Surveillance Reform Act (GSRA), and the inclusion of a broad warrant requirement and other reforms within a House Judiciary Committee reform bill now being drafted. As this story makes clear, we must have these reforms before any extension of Section 702 of the Foreign Intelligence Surveillance Act can be contemplated. Revival of Notorious ‘Lone Wolf’ Spying on Americans’ Browsing, Biometrics? The intelligence community and its champions on Capitol Hill are frantic, perhaps even panicked, as they see the approach of the end-of-the-year deadline for the reauthorization of Section 702 of the Foreign Intelligence Surveillance Act. The result is a furious throw-spaghetti-at-the-wall strategy in a vain effort to get something to stick – as long as it doesn’t look like reform.
At the heart of this controversy is whether this authority – enacted by Congress to enable the surveillance of foreigners on foreign soil – should require a probable cause warrant, as mandated by Fourth Amendment, when the government examines Americans’ personal communications collected under Section 702. The White House declared that a warrant for such U.S. person queries would constitute a “red line.” It is not clear, however, if President Biden would actually follow through on his threat to veto the reauthorization of Section 702. FBI Director Christopher Wray in prepared remarks said that having a warrant requirement would entail “profound risks,” forcing the expenditure of “scarce resources, the submission and review of a lengthy legal filing, and the passage of significant time – which, in the world of rapidly evolving threats, the government does not always have.” He is contradicted by David Aaron, former senior attorney for the Department of Justice National Security Division. Aaron wrote that a warrant requirement would be “a relatively light burden on the government.” Beyond rhetoric, the champions of the intelligence community in Congress last Sunday tried to attach a “clean” – that is, an unchanged extension of Section 702 without reforms – into the budgetary continuing resolution. This resulted in an immediate response from leading champions of civil liberties and a determined pushback from almost thirty civil liberties organizations from left, right, and center. When that failed, the opponents of reform pivoted and proposed attaching their extension of Section 702 in the must-pass National Defense Authorization Act (NDAA). PPSA’s Senior Policy Advisors Bob Goodlatte, former Chairman of the House Judiciary Committee, and Mark Udall, who served on the Senate Select Committee on Intelligence, dispatched a letter to Members warning against this legislative legerdemain. The threat of such an extension of Section 702 in the NDAA seems to have now receded. Also last week, the House Permanent Select Committee on Intelligence released a bill disingenuously labeled a reform bill. It contains a warrant requirement limited to a narrow subset of “evidence of a crime” surveillance queries, while allowing the FBI to continue to define pretty much anything else as a matter of national security worthy of warrantless surveillance. This leaves unclear how the FBI would meet the bill’s evidence-of-a-crime warrant standard but not a broader warrant requirement. This measure appears to be intentionally designed to be either taken out of the bill or simply ignored by the FBI in practice. As Sen. Mike Lee notes, the House Intelligence bill is “window dressing” to “expand government surveillance.” Under the House Intelligence Committee’s bill, the FBI might continue practices that led to batch queries of current and former federal government officials, journalists, political commentators, and 19,000 donors to a congressional campaign. Another expansion in the bill is its restoration of “Lone Wolf Surveillance” authority, the suspicionless monitoring of online searches, social media usage, and increasingly unique biological traits such as facial recognition, DNA, and even analysis of body language to catch the solitary terrorist. ACLU’s Matthew Harwood wrote in 2015 that this approach “would represent a fundamental assault on a free society. Such ‘countermeasures’ should send a shiver down your spine … The dangers to Americans in allowing government agencies to collect such intimate information in order to discover whether any of them are possible lone wolves should be obvious in terms of the destruction of privacy, among other things. The result would be both an Orwellian world and a hopeless one in safety terms.” Drawing on data from multiple studies, Harwood wrote: “It’s already clear that none of these expensive and advanced technological ‘solutions’ will work. Totally innocent conduct (‘false positives’) will overwhelm the truly menacing.” Expect champions of the intelligence community to continue to pull out all the stops, from backroom legislative maneuvers to more non-reform “reform” proposals. They will continue until more Americans contact their House and Senate Members and demand passage of a real reform measure, such as the Government Surveillance Reform Act – which upholds the Constitution’s requirement for a probable cause warrant for Americans’ communications, location and vehicle data, web browsing, and search records, while allowing reasonable exceptions for cybersecurity and emergency situations. Soon, the House Judiciary Committee will also be releasing a true reform bill, as well. Let Congress know where you stand. Late last week, word began to circulate that the Senate majority is considering including Section 702 of the Foreign Intelligence Surveillance Act in a Continuing Resolution (CR). On Monday morning, a broad coalition of civil liberties groups – left, right and center – sent a letter to Majority Leader Chuck Schumer urging him and the Senate not to include Section 702 in the CR or any must-pass legislation.
Bob Goodlatte, PPSA Senior Policy Advisor and former Chairman of the House Judiciary Committee, explained why PPSA joined in this effort in a media statement. Goodlatte said: “We’ve seen how short-term extensions have a habit of becoming long-term. Extending Section 702 in the CR risks a clean reauthorization of Section 702 with no reforms. “If that happens, expect the FBI to get back to business as usual. Expect warrantless FBI surveillance of Members of Congress and Americans exercising their First Amendment rights to continue. Including Section 702 in the CR would also cut reform off at the knees. It would short-circuit bipartisan reformers in the House and Senate, including critical legislative efforts by the House Judiciary Committee and by dozens of Senators and House Members who’ve worked in good faith to balance national security with our constitutional rights. “Upending these reform efforts would not only lead to a new wave of abuses under Section 702 or other parts of FISA – it would also enable federal agencies to increasingly surveil Americans by accessing our most sensitive personal data, scraped from apps, and sold to the government by shadowy data brokers. “For all these reasons, it would be a terrible mistake to include Section 702 in a CR or any other must-pass legislation.” Four experts on civil liberties, including PPSA’s general counsel Gene Schaerr, explored the tension between liberty and safety at a Federalist Society discussion on Section 702 of the Foreign Intelligence Surveillance Act on Friday. A newsworthy declaration was made by Beth Williams, board member of the government watchdog, the Privacy and Civil Liberties Oversight Board (PCLOB) about balancing Section 702 reform with national security. Williams called Section 702 a “highly valuable” program that “provides irreplaceable intelligence” that generates two-thirds of the president’s daily intelligence briefing. Williams added that all five PCLOB members, while disagreeing on many points, agreed that: “While Section 702 is not a bulk collections program, we agreed that reforms to the program are in order to fix some problems with its operation, particularly by the FBI and to prevent its possible misuse for political and other improper purposes. This can be done without degrading the value of the program.” This was a notable declaration given that Williams and board member Richard DiZinno had dissented from PCLOB Chair Sharon Bradford Franklin and the board’s majority on the need for warrant requirements and other reforms. Williams’ remarks validated a statement by Chair Franklin that no PCLOB member “has called for the program to lapse and also no board member has called for clean reauthorization of the program." A sharp divergence in world views emerged between the constitutional vision of Gene Schaerr and a dark, dystopian future suggested by former NSA lawyer Stewart Baker. Schaerr kicked off this part of the discussion by asking the Federalist Society audience to conduct a thought experiment by imagining what James Madison would say if we could bring him up back to life and up to speed about the many ways the FBI has to surveil Americans. “He would be horrified,” Schaerr said by the denigration of the Fourth Amendment and the breakdown between congressional and executive powers. Schaerr imagined Madison reminding us that the founders “decided that way we set up this government would be to accept some inefficiencies as the price of freedom.” Baker posited a world in which artificial intelligence enables anyone who wants to develop more lethal toxins and infectious diseases to do so, a world of weapons of mass destruction in the hands of “disgruntled teenagers.” Baker’s reply to Schaerr’s thought experiment: “I don’t think James Madison would come back and say, ‘well, you’re just going to have to live in my world and suffer 21st century consequences.’” Gene Schaerr listed the “multipronged” ways the FBI can surveil Americans – from Section 702 information, to personal, sensitive data scraped by apps and purchased by the FBI and other government agencies from data brokers, to executive orders that allow the government to extract Americans’ texts, emails, and browsing histories from the cloud. Given the pervasive reach of such government surveillance, are the alarming fears of technology and hostile actors reason to give up on the Constitution and live in a surveillance state? This discussion leaves us to decide: Do you agree with Stewart Baker, that we must embrace pervasive surveillance to survive? Or do you agree with Gene Schaerr, who concluded: “We can realign federal government surveillance powers with the founders’ vision of what our government can be.” Watch: The Ninth Circuit Court of Appeals in March issued a controversial opinion in Twitter v. Garland that the Electronic Frontier Foundation calls “a new low in judicial deference to classification and national security, even against the nearly inviolable First Amendment right to be free of prior restraints against speech.”
X (née Twitter) is appealing this opinion before the U.S. Supreme Court. Whatever you think of X or Elon Musk, this case is an important inflection point for free speech and government surveillance accountability. Among many under-acknowledged aspects of our national security apparatus is the regularity with which the government – through FBI national security letters and secretive FISA orders – demands customer information from online platforms like Facebook and X. In 2014, Twitter sought to publish a report documenting the number of surveillance requests it received from the government the prior year. It was a commendable effort from a private actor to provide a limited measure of transparency in government monitoring of its customers, offering some much-needed public oversight in the process. The FBI and DOJ, of course, denied Twitter’s efforts, and over the past ten years the company has kept up the fight, continuing under its new ownership. At issue is X’s desire to publish the total number of surveillance requests it receives, omitting any identifying details about the targets of those requests. This purpose is noble. It would provide users an important metric in surveillance trends not found in the annual Statistical Transparency Report of the Office of the Director of National Intelligence. Nevertheless, in April 2020, a federal district court ruled against the company’s efforts at transparency. In March 2023, the Ninth Circuit upheld the lower court’s ruling, sweeping away a substantial body of prior restraint precedent in the process. Specifically, the Ninth Circuit carved out a novel exemption to long established prior restraint limitations: “government restrictions on the disclosure of information transmitted confidentially as part of a legitimate government process.” The implications of this new category of censorable speech are incalculable. To quote the EFF amicus brief: “The consequences of the lower court’s decision are severe and far-reaching. It carves out, for the first time, a whole category of prior restraints that receive no more scrutiny than subsequent punishments for speech—expanding officials’ power to gag virtually anyone who interacts with a government agency and wishes to speak publicly about that interaction.” This is an existential speech issue, far beyond concerns of party or politics. If the ruling is allowed to stand, it sets up a convenient standard for the government to significantly expand its censorship of speech – whether of the left, right or center. Again, quoting EFF, “[i]ndividuals who had interactions with law enforcement or border officials—such as someone being interviewed as a witness to a crime or someone subjected to police misconduct—could be barred from telling their family or going to the press.” Moreover, the ruling is totally incongruous with a body of law that goes back a century. Prior restraints on speech are the most disfavored of speech restrictions because they freeze speech in its entirety (rather than subsequently punishing it). As such, prior restraint is typically subject to the most exacting level of judicial scrutiny. Yet the Ninth Circuit applied a lower level of strict scrutiny, while entirely ignoring the procedural protections typically afforded to plaintiffs in prior restraint cases. As such, the “decision enables the government to unilaterally impose prior restraints on speech about matters of public concern, while restricting recipients’ ability to meaningfully test these gag orders in court.” We stand with X and EFF in urging the Supreme Court to promptly address this alarming development. The Government Surveillance Reform Act (GSRA) Four bipartisan champions of civil liberties – Sen. Ron Wyden (D-OR), Sen. Mike Lee (R-UT), Rep. Warren Davidson (R-OH) and Rep. Zoe Lofgren (D-CA) – today introduced the Government Surveillance Reform Act (GSRA), legislation that restores force to overused Capitol Hill adjectives like “landmark,” “sweeping,” and “comprehensive.”
“The Government Surveillance Reform Act is ambitious in scope, thoughtful in its details, and wide-ranging in its application,” said Bob Goodlatte, former Chairman of the House Judiciary Committee and PPSA’s Senior Policy Advisor. “The GSRA is a once-in-a-generation opportunity for wide-ranging reform.” The GSRA curbs the warrantless surveillance of Americans by federal agencies, while restoring the principles of the Fourth Amendment and the policies that underlie it. The authors of this bill set out to achieve this goal by reforming how the government uses three mechanisms to surveil the American people.
The GSRA will rein in this ballooning surveillance system in many ways.
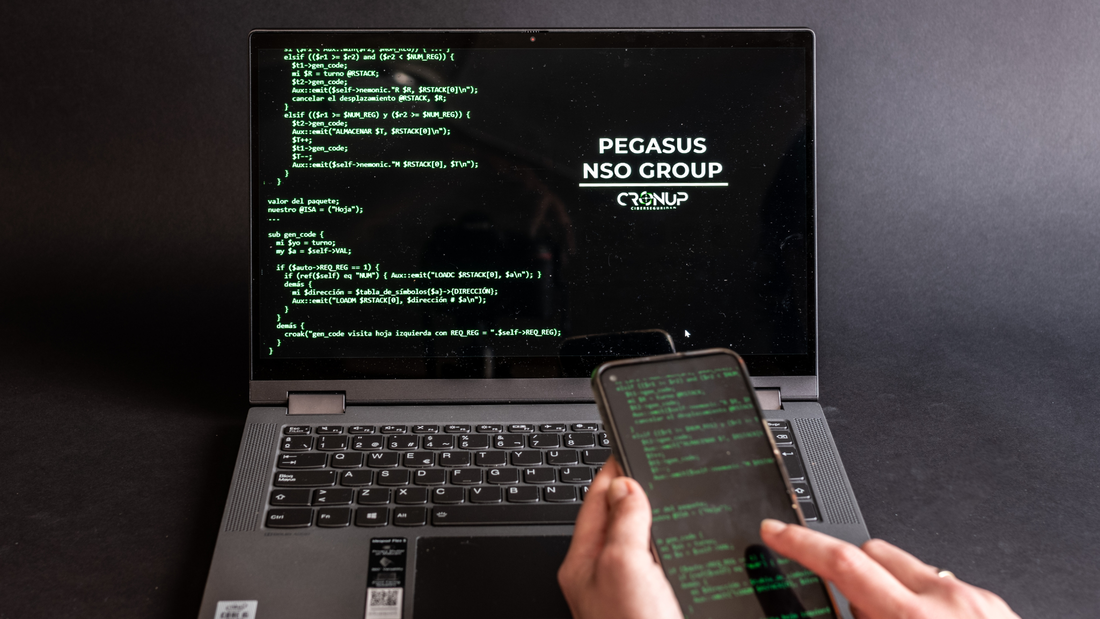
“The GSRA enjoys widespread bipartisan support because it represents the most balanced and comprehensive surveillance reform bill in 45 years,” Goodlatte said. “PPSA joins with a wide-ranging coalition of civil liberties organizations to urge Congress to make the most of this rare opportunity to put guardrails on federal surveillance of Americans. “We commend Senators Wyden and Lee, and Representatives Davidson and Lofgren, for writing such a thorough and precise bill in the protection of the constitutional rights of every American.” Apple Sends Notice of Hack Pegasus – the Israeli-made spyware – continues to proliferate and enable bad actors to persecute journalists, dissidents, opposition politicians, and crime victims around the world.
This spyware transforms a smartphone into the surveillance equivalent of a Swiss Army knife. Pegasus has a “zero-day” capability, able to infiltrate any Apple or Android phone remotely, without requiring the users to fall for a phishing scam or click on some other trick. Once uploaded, Pegasus turns the victim’s camera and microphone into a 24/7 surveillance device, while also hoovering up every bit of data that passes through the device – from location histories to text, email, and phone messages. We’ve written about how Mexican cartels have used Pegasus to track down and murder journalists. We’ve covered the role of Pegasus in the murder of Saudi dissident Adnan Khashoggi, and how an African government used it to spy on an American woman while she was receiving a briefing inside a State Department facility on her father’s abduction. Now fresh evidence from Apple alerts shows how Pegasus continues to be used by governments to spy on political opponents. Journalists have learned that the Israeli-based NSO Group has sold its spyware to at least 10 governments. Two years ago, it was revealed that a government had used Pegasus to surveil Spanish politicians, including the prime minister, as well as regional politicians. Now it is happening in India. On Oct. 31, just in time for Halloween, Apple sent notices to more than 20 prominent journalists, think tank officials, and politicians in opposition to Prime Minster Narenda Modi that hacking attempts had been made on their smartphones. In 2021, The Washington Post and other media organizations investigated a list obtained by Forbidden Stories, a Paris-based non-profit media outlet, tracking down more than 1,000 phone numbers of hundreds of prominent Indians who were set to be surveilled by Pegasus. This plan now seems to have been executed, at least in part. “Spyware technology has been used to clamp down on human rights and stifle freedom of assembly and expression,” said Likhita Banerj of Amnesty International. “In this atmosphere, the reports of prominent journalists and opposition leaders receiving the Apple notifications are particularly concerning in the months leading up to state and national elections.” Yesterday Spain, today India, tomorrow the United States? It is public knowledge that the FBI owns a copy of Pegasus and that a recent high-level government attorney from the intelligence community has signed on to represent the NSO Group. This is all the more reason for Congress to pass serious reforms to Section 702 of the Foreign Intelligence Surveillance Act, to curtail all forms of illicit government surveillance of Americans. PPSA will continue to monitor this story. When FBI Director Christopher Wray came under heated questioning during his testimony Tuesday before the Senate Homeland Security and Governmental Affairs Committee, he let slip a remark likely to haunt him for the rest of the debate over proposed reforms to Section 702 of the Foreign Intelligence Surveillance Act (FISA).
Director Wray said, “With everything going on in the world, imagine if a foreign terrorist overseas directs an operative to carry out an attack here on our own backyard, but we’re not able to disrupt it because the FBI’s authorities have been so watered down.” By “watered down” Wray meant reformers’ proposal requiring the FBI to meet the Fourth Amendment’s requirement to obtain a probable cause warrant before accessing the private communications of Americans taken from Section 702. This authority was enacted by Congress to enable surveillance of foreign terrorists and spies located on foreign soil. There is no reason why Section 702 cannot be used to surveil “a foreign terrorist overseas.” The problem is that this authority has become a prime resource for the FBI and other agencies to warrantlessly review the information of Americans. Sen. Rand Paul (R-KY), Ranking Member on the committee, responded: “You would think we’d be going after foreigners, but we are using the Foreign Intelligence Surveillance Act to go after Americans.” In addition to skepticism from Sen. Paul and others on the committee, Director Wray’s assertions are contradicted by others with experience in FISA. In a recent editorial, Sharon Bradford Franklin, chair of the independent government watchdog group, the Privacy and Civil Liberties Oversight Board (PCLOB), with two other board members in a recent Washington Times editorial, supported requiring a court order or warrant before the government can review Americans’ Section 702 data. The PCLOB members noted that “the FBI has repeatedly violated querying rules to run searches on Americans. This includes impermissible searches for members of Congress, those who protested the murder of George Floyd, preachers, participants in an FBI community relations program, victims who reported crimes …The FBI has failed to get this right for more than a decade. The bureau’s persistent noncompliance over the years dramatically illustrates the need for independent, impartial, and external review. These compliance errors may also undermine the public’s trust in the FBI, raising real questions about its ability to police itself.” In his written testimony, Director Wray also informed the committee that a warrant requirement would amount to a “de facto ban” on U.S. person queries because warrants are so difficult to obtain from a court. Would a warrant requirement necessarily be a “ban” that would “water down” the FBI’s ability to protect Americans? David Aaron, who held several senior legal positions at the Department of Justice’s National Security Division, wrote in Just Security that “requiring the government to establish probable cause and obtain judicial approval before searching for U.S. person’s communications within previously collected material would bolster that confidence and is a relatively light burden on the government.” A majority in Congress clearly agree. None other than Senate Judiciary Chairman Dick Durbin (D-IL) has said he will only support Section 702 reauthorization if there are “significant reforms,” including “first and foremost, addressing the warrantless surveillance of Americans in violation of the Fourth Amendment.” Or, as Chair Franklin and her colleagues wrote: “We do not permit the police to break into a home without such court approval, and we should not permit government personnel to access our communications through U.S. person queries without court review. This is Civics 101.” Sen. Paul told Wray: ”I fear that our federal government is still undertaking many of the same tactics that the Church Committee found to be unworthy of democracy.” Perhaps it is the Fourth Amendment that has been watered down. Is the Executive Branch Targeting Oversight Committees? PPSA continues to press a Freedom of Information Act (FOIA) request seeking documents that would shed light on the extent to which the executive branch is spying on Members of Congress. We are asking the government for production of documents on “unmasking” and other forms of government surveillance of 48 current and former House and Senate Members on committees that oversee the intelligence community.
Now the court and Congress have fresh reason to give the issue of executive branch spying on Congress and its oversight committees renewed attention. Jason Foster, the former chief investigative counsel for Sen. Chuck Grassley – the Ranking Member of the Senate Judiciary Committee – recently learned that he is among numerous staffers, Democrats as well as Republicans, who had their personal phone and email records searched by the Department of Justice in 2017. A FOIA request filed by the nonprofit Empower Oversight, founded by Foster, seeks documents concerning the government’s reasons for compelling Google to reveal the names, addresses, local and long-distance telephone records, text message logs and other information about the accounts of congressional attorneys who worked for committees that oversee DOJ. The government’s subpoena also compelled the release of records indicating with whom each user was communicating. The Empower Oversight FOIA notes: “This raises serious public interest questions about the basis of such intrusion into the personal communications of attorneys advising congressional committees conducting oversight of the Department. Constitutional separation of powers and privilege issues raised by the Speech or Debate Clause of (U.S. Const. art I. § 6) and attorney-client communications of those targeted with these subpoenas should have triggered requirements for enhanced procedural protections and approvals.” As The Wall Street Journal noted in an editorial, these subpoenas coincided with leaks of classified information concerning a wiretapped phone call between incoming Trump national security adviser Michael Flynn and the Russian ambassador. This leak was investigated by the Senate Judiciary Committee. Many now wonder if DOJ’s dragnet of personal information of congressional staffers was an attempt at misdirection, perhaps a fishing expedition to find someone else to blame. Empower Oversight’s FOIA states: “If the only reason the Justice Department targeted the communications of these congressional attorneys was their access to classified information that was later published by the media, it raises the question of whether the Department also subpoenaed the personal phone and email records of every Executive Branch official who had access to the same information.” The Empower Oversight FOIA concludes about this surveillance of Congressional staff: “It begs the question whether DOJ was equally zealous in seeking the communications records of its own employees with access to any leaked document.” Sen. Grassley, who aggressively pursues government surveillance overreach, will likely want to follow up on these questions. In the meantime, PPSA petitions the D.C. Circuit Court for an en banc hearing on the possible unmasking and other surveillance of some of the elected bosses of these congressional attorneys. The Colorado Supreme Court issued a 5-2 ruling that leaves an urgent privacy question wreathed in a cloud of ambiguity. As a result, Americans must worry that merely being in the same location as someone who might have done an internet search for suspicious material could end up with their own search data being examined by the police.
So-called “reverse warrants” are a powerful new type of search warrant enabled by the collection of Americans’ private data. Reverse warrants allow the police to sift through the search histories of thousands of people. They come in two types: geofence warrants, which allow police to identify people whose devices were in a certain area at a certain time, and reverse keyword warrants, which allow police to identify who searched certain keywords, phrases, or addresses online. These warrants and their underlying technologies allow police to track any person and search through their data. Instead of developing suspicions about a person based on factual evidence and then applying for a warrant to search that specific person – as required by the Fourth Amendment – reverse warrants involve looking through the search history or location history of many innocent people in the hopes of finding a suspect. Reverse warrants exist in legal limbo. There is little precedent or written law that govern this new form of data analysis. Accordingly, some courts have treated reverse warrants as they would any standard warrant. Seymour v. Colorado is the first case to address the constitutionality of reverse warrants. This case springs from a particularly heinous crime – an arson that killed a family of five. Two months later, the Denver Police Department obtained a reverse keyword warrant. As a result of the warrant, Google was forced to hand over the data of eight people, five of whom had Colorado-based IP addresses that had searched for the location of the arson in a two-week period before the crime. Three suspects were eventually charged. One of them, Gavin Seymour, sued to suppress evidence obtained by the warrant on constitutional grounds. The court held that “Seymour has a constitutionally protected privacy interest in his Google search history,” and that “Seymour’s Google search history implicates his right to freedom of expression.” The court also found that law enforcement obtained and executed the warrant in good faith, so the evidence shouldn’t be suppressed under the exclusionary rule. Thus the court acknowledged the serious constitutional issues at play and still treated the reverse warrant as if it was just an ordinary search. The court stated that “the warrant required individualized probable cause and that its absence here rendered the warrant constitutionally defective.” Yet, somehow, it was still admissible evidence. Five innocent people had their data searched. Another five innocent people were murdered in a fire. There is a lot at stake in this case, and a lot to unpack. Does a search of Google search histories by a given address satisfy the Constitution’s requirement for a particularized search? Can probable cause be asserted when the identity of the suspect is unknown? Could digital bystanders have evidence used against them from a search result unrelated to this particular crime? Perhaps this case will advance to the U.S. Supreme Court, which could take this opportunity to articulate boundaries and rules for future searches. We’ve seen, however, a time lag in the Court’s addressing of new technologies. Congress should consider taking measures to protect privacy in reverse warrants before the Supreme Court is forced to weigh in. The Congressional debate over the reauthorization of Section 702 of the Foreign Intelligence Surveillance Act (FISA) has mostly centered around the outrage of federal agencies using an authority meant for the surveillance of foreigners on foreign soil to warrantlessly collect the communications of hundreds of thousands of Americans every year.
But the Section 702 debate highlights an even greater outrage that needs to be addressed – the routine practice by federal agencies to purchase and access the private data of Americans scraped from our apps and devices without a warrant. While federal data purchases are not part of Section 702, history suggests that any reforms made to Section 702 to curtail the surveillance on Americans in the pool of “incidentally” collected communications will be futile if we don’t close this other loophole. Our data, freely collected and reviewed at will by the government, can be more personal than a diary – detailing our medical concerns, romantic lives, our daily movements, whom we associate with, our politics and religious beliefs. The Wall Street Journal shined a much-needed light on this practice. It reported on the relationship between U.S. government agencies and the shadowy world of data-broker middlemen who peddle our most sensitive personal information. The Journal reported that India-based Near Intelligence has been “surreptitiously obtaining data from numerous advertising exchanges” and selling this data to the NSA, Joint Special Operations Command, the Department of Defense, and U.S. Air Force Cyber Ops. The Journal accessed a memo from Jay Angelo, Near Intelligence general counsel and chief privacy officer, to CEO Anil Mathews about three privacy problems. First, Angelo wrote that Near Intelligence sells “geolocation data for which we do not have consent to do so.” Second, he wrote the company sells or shares “device ID data for which we do not have consent to do so.” And, finally, Angelo wrote, the company violates the privacy laws of Europe by selling Europeans’ data outside of Europe. Customers include agencies of the U.S. federal government, which “gets our illegal EU data twice per day.” It is unclear the extent to which this company sells Americans’ data, though it seems likely that the privacy of Americans is implicated given that the company boasts of having access to data from a billion devices. Near Intelligence is just one actor in this shadowy world of merchants of personal data. Congress should require government agencies to obtain a probable cause warrant to examine the private data of Americans, whether collected under Section 702 or through data purchases. Shameless Opportunism...The intelligence community is now spinning the media that the barbarous invasion of Israel and mass murder of its citizens by Hamas should prompt Congress to reauthorize Section 702 of the Foreign Intelligence Surveillance Act without any meaningful changes or reforms.
Before listening to the intelligence community’s spin, Congress should first ask why given this powerful Section 702 authority and all the technology in the hands of the NSA, did U.S. intelligence miss the scale and scope of Hamas’ intentions? While U.S. intelligence detected rising activity in Gaza, it did not detect the threat that resulted in the killing of more than 1,400 Israelis and at least 30 Americans. Instead of explaining this abject intelligence shortfall, some in the intelligence community are defaming champions of Section 702 reform on Capitol Hill as opposing surveillance of Hamas. This weak attempt to deflect from an abject failure makes no sense. It is, at best, an especially callous perversion of Rahm Emanuel’s aphorism that one should “never let a good crisis go to waste.” Carrie Cordero, a CNN legal and national security analyst, and former counsel at the Office of the Director of National Intelligence, writes: “Hamas, Hezbollah and their state-sponsor, Iran, are wholly appropriate intelligence targets, and Section 702 authority should not be degraded while threats from these actors have escalated to the degree of starting a new war in the Middle East.” In just a few words, Cordero portrays the many House and Senate Members in both parties who are pushing to add warrants for Americans to the reauthorization of Section 702 as being willing to “degrade” an authority that counters some of the worst regimes in the world. This broadside obfuscates the purpose of Section 702 and how it is being misused by our government to spy on the American people. Congress designed Section 702 to create a legal authority for U.S. intelligence agencies to spy on foreigners located abroad for national security purposes. It is, as Cordero notes, a tool especially designed for counterterrorism. No reform on the table would restrict U.S. intelligence from using Section 702 to surveil Hamas, Hezbollah, Iran, Russia, China, North Korea, or the devil himself. So how, then, could reforms to Section 702 “degrade” this important and useful authority? There can be only one meaning to this phrase. Somehow, protecting the rights of American citizens against intrusive and unconstitutional spying would “degrade” Section 702. Civil liberties groups and their champions on the Hill are concerned that this authority, meant to surveil foreign threats on foreign soil for national security, has been used by the FBI to spy on a Member of the U.S. House, a Member of the U.S. Senate, 19,000 donors to a congressional campaign, community leaders, and protest groups both left and right. The FBI also uses Section 702 to warrantlessly access the communications of Americans to obtain a backdoor route to prosecuting them for ordinary crimes, such as bribery and healthcare fraud – far beyond the intention of Congress in passing Section 702. In the hands of the FBI, Section 702 has turned the Fourth Amendment requirement for a probable cause warrant for American citizens into vaporware. Fixing this would do nothing to degrade the ability of the CIA to follow Hamas and Hezbollah, or to restrain the FBI from obtaining a warrant to surveil an American who is in communication with dangerous actors. That they now want to use their failure as an excuse to violate the civil liberties of law-abiding U.S. citizens – by the hundreds of thousands each year – speaks to shameless opportunism, masking incompetence and authoritarian tendencies. Myths vs. Facts: Has the FBI Fixed What Is Wrong with Section 702 with Internal Procedures?10/10/2023
Intelligence Community MYTH: The FBI has new minimization procedures that have dramatically reduced the numbers of U.S. person queries in the Section 702 database and the potential for violations. No fixes in the law are needed.
FACT: Even FBI Director Christopher Wray’s brag that refinements in internal procedures have reduced the number of warrantless searches for Americans’ communications to approximately 204,000 queries of Americans’ personal communications per year is alarming. The number of people who have been victimized by these civil rights violations is equal to the population of many medium-sized U.S. cities. As Sen. Mike Lee says, “That number should be zero. Every ‘non-compliant’ search violates an American’s constitutional rights.” Jonathan Turley of the George Washington University Law School dismissed the FBI’s recent boasts about the reduced number of improper queries into Americans’ private information, likening that boast to “a bank robber saying we’re hitting smaller banks.” The many broken promises of the FBI should leave the bureau with little room for a “trust me” clean reauthorization of Section 702. Consider the government’s long history of abuses. In just the last few years, in violation of its own rules:
Other actions outside Section 702, such as the wide-ranging politically motivated investigation of “radical traditional Catholics,” further reveal an FBI appetite for playing politics. Nobody in their right mind should want the FBI to have warrantless access to their private sensitive personal communications and data. As Congress debates the reauthorization and reform of Section 702 of the Foreign Intelligence Surveillance Act (FISA), Members should keep in mind an instructive example from a local government that shows just how personal mass surveillance abuse can be.
During the pre-vaccine, early Covid era, Calvary Chapel San Jose in Santa Clara County, California, continued to hold regular worship services with hundreds of unmasked congregants, in defiance of official shelter-in-place orders. The county reacted by seeking north of $1 million dollars in fines against the non-denominational church, an action now wending its way through court. Not content to fine the church, or warn congregants, Santa Clara County mounted a large surveillance campaign that managed to compromise both the Fourth Amendment rights of the congregants against unreasonable searches and seizures, while also compromising their First Amendment right to the free exercise of religion. Some of the spying was physical, with county agents making 44 visits to Calvary Chapel in 2020 and 2021. Agents also parked a surveillance car in the parking lot of a nearby church, until they were asked to leave. The county then turned to invasive and warrantless geofencing, using Safegraph software to track local citizens’ cellphones on church premises, following churchgoers as they went to the sanctuary room, nursery, the prayer room, even to the bathroom. In a federal lawsuit against the county, the church’s complaint noted that location data reveals more than a target’s physical movements. It also shows “a person’s pattern of life. These tools provide a story about where and with whom people socialize, visit, worship, and much more.” Data scientists tested just how anonymous geolocation data really is. Researchers at Imperial College London developed a machine learning model that was able to correctly re-identify 99.98 percent of Americans in any anonymized dataset using just 15 characteristics including age, gender, and marital status. In another study that investigated smartphone location data, researchers were able to uniquely identify 95 percent of the individuals in a dataset with just four spatio-temporal points. It is hard, then, to say the church exaggerates when it informs the court in its filing that “this is not just un-American; it is downright Orwellian.” This surveillance was apparently done not to investigate a crime, which requires the government to obtain a warrant, limited in time and scope. It was done to give the county data information it could weaponize against the church in its ongoing lawsuit for violating public health orders. Whatever one thinks of the church’s defiance of the county’s orders, the warrantless use of geolocation surveillance against hundreds of local residents is an example of how reckless government at all levels can be with widely available technology. “There are all kinds of concerns with geofencing when you talk about your First Amendment rights like freedom of expression or freedom of religion,” Mike Katz-Lacade of the Center for Human Rights and Privacy told The San Jose Mercury News. “You could conceivably use it to see who goes to a mosque – or discriminate against certain religious groups or minorities.” These same geolocation tools are widely available to federal intelligence and law enforcement agencies, which can either deploy them or simply buy the underlying data of our location tracked by our phones and apps. Thus, this local story is one of national significance. It is something to keep in mind in debating needed changes to Section 702, the authority Congress designed for foreign surveillance but which the FBI uses routinely to conduct criminal investigations of Americans. Intelligence Community MYTH: Warrantless access to Americans’ data is vital to defending people and companies against cyberattacks and ransomware. Otherwise, we’d be wide-open to cyberattacks from Russia and China.
FACT: Most cybersecurity experts disagree with the government’s argument. The Washington Post conducted a survey of “a group of high-level digital security experts from across government, the private sector and security research community.”
There is no “defensive” exception to the Fourth Amendment. The fact that the government claims to be doing something for our own good does not make it constitutional, nor does it mitigate the privacy intrusion or risk of abuse. If government agents want to access our private communications for our own good, they should simply ask our permission. Without that permission, they should get a probable cause warrant to spy on Americans’ communications. PCLOB Chair Ups Ante by Calling for Probable Cause Warrant for U.S. Person Queries What are the topline takeaways from the report from the Privacy and Civil Liberties Oversight Board (PCLOB) on Section 702 of the Foreign Intelligence Surveillance Act (FISA)?
A majority of board members of this government watchdog panel directly counter the claims of the Biden Administration and the intelligence community that a requirement for the government to seek judicial review of the private communications of Americans would be “operationally unworkable” and lead to extreme danger to national security. The report punctures the FBI’s frequent claims that having the ability to rifle through Americans’ communications without a warrant is essential to national security and protecting the United States from harm. The PCLOB majority endorses “individualized and particularized judicial review” by the FISA Court before the government can review data of U.S. citizens and legal residents. PCLOB is coming down firmly on the side of civil liberties organizations that have long argued against intelligence and law enforcement agencies being allowed to have ready access to Americans’ private data and communications, with little judicial oversight. Internal FBI Procedures Insufficient The PCLOB majority finds the internal changes by the FBI in its Section 702 procedures to be far less than what is needed to protect Americans from backdoor searches, the practice of using secretly derived information to develop a case. Moreover, these searches are generally useless, as are the FBI’s internal procedures. The report also rejects that broad categories of searches, such as so-called “defensive” searches for potential victims’ information, should be exempted from judicial review. Amici, Abouts and Unmasking The report endorses the proposal to require amici – or qualified civil liberties experts to advise the FISA Court whenever proposed investigations touch sensitive cases that implicate basic constitutional rights. The board would narrow the standards by which the government selects targets. And the board would formally restrict “abouts” collection – information in which a target is merely mentioned. Even the two board members who voted against the report found that “The U.S. Intelligence Community should adopt new rules to protect against the unmasking of U.S. Persons for political purposes.” The Chair’s Call for a Warrant Requirement Chair Sharon Bradford Franklin (see p. 226) writes that a “search through Section 702 communications data seeking information about a particular American constitutes a search under the Fourth Amendment, and current query standards are insufficient to meet constitutional requirements.” Chair Franklin notes that the FBI routinely runs searches of U.S. persons at a preliminary stages of an inquiry. The FBI “asserted that it could not meet a probable cause standard for such queries conducted at these early stages.” Nor could the FBI identify, outside the categories of “victim” or “defensive” queries, “a single criminal prosecution that relied on evidence identified through a U.S. person query.” Chair Franklin raises the ante on PCLOB’s recommendation that a FISA Court provide judicial review for U.S. person queries. “But I believe that Congress should also require a probable cause standard for FBI’s U.S. person queries conducted at least in part to seek evidence of a crime in order to fully protect Americans’ privacy and civil liberties.” Franklin writes that this is the only way to ensure such queries fully comply with the Fourth Amendment, while being consistent with criminal law in other contexts. She would explicitly adopt the standards of Carpenter v. United States (2018), in which the U.S. Supreme Court held that the police don’t need a warrant to seize a cellphone but do need a warrant to search the contents of that cellphone, which contain “the privacies of life.” She analogizes this case to the “seizure” of the incidental collection of Americans’ information under Section 702, and the need to have a warrant to search it. Chair Franklin’s conclusions, and the PCLOB’s full list of 19 recommendations, are included in the executive summary of its report. Intelligence Community MYTH: We need to reauthorize Section 702 of the Foreign Intelligence Surveillance Act – just as it is now – in order to counter the carnage caused by fentanyl trafficking.
FACT: The government hasn’t cited a single instance in which warrantless searches of Americans’ communications proved useful in combating the fentanyl trade. None of the proposed surveillance reforms involving Americans’ privacy, such as a warrant requirement, would stop the intelligence community from using Section 702 to locate foreign fentanyl labs, whether in China or Mexico, and tracking the cartels that smuggle it. And if an American does become a suspect in this trafficking, the government can and should seek a probable cause warrant, as is routinely done in other domestic law enforcement cases. We do not need to sacrifice our constitutional rights in order to fight fentanyl trafficking. Intelligence Community MYTH: To talk about anything other than Section 702 during the reauthorization debate is a distraction.
FACT: Section 702 is only one of many ways the government collects and searches through Americans’ private communications and data without a warrant. If we do not close all the loopholes that allow for illicit surveillance, then the government will seamlessly shift over to alternate ways of watching our every action, move, and utterance. One of the most dangerous forms of lawless surveillance is the widespread practice of government agencies buying up Americans’ sensitive digital communications, geolocation histories, and other private information from third-party data brokers. Federal agencies from the IRS, to DHS, FBI, DEA and DoD routinely purchase and access data of American consumers scraped from apps and social media to review our online search histories, location histories, and communications from texts to phone calls and emails. The government, for example, has purchased data from religious apps and dating apps. Government attorneys assert that this is lawful because the Fourth Amendment forbids “seizures” of our papers and effects, when in fact they are merely buying it. This sophistry must be countered. We should extend a warrant requirement to data purchases under Section 702 to keep the intelligence community from shifting to a reliance on purchased data or some other authority largely unconstrained by judicial and Congressional oversight. The government also surveils American citizens through Executive Order 12333 – not a law, just an assertion of authority by the executive branch – with very little (if any) oversight from Congress. Former Sen. Richard Burr (R-NC), a noted champion of the intelligence community, said on the Senate floor in 2020 that 12333 authority allows “the president to do all of this, without Congress’s permission, without guardrails.” The Section 702 reauthorization is our best opportunity to rein in these and other forms of warrantless surveillance. It is imperative that Congress act on this opportunity. If legislative reforms are narrowly limited to Section 702, the Administration will simply rely more heavily on these loopholes to continue its lawless surveillance of Americans. Congress intended Section 702 of the Foreign Intelligence Surveillance Act (FISA) to give U.S. intelligence agencies the authority to collect intelligence from foreigners located abroad.
For fifteen years, however, federal agencies have exploited Section 702 and other surveillance programs to conduct warrantless surveillance on millions of Americans. The numbers are staggering: In 2021 the FBI conducted 3.4 million warrantless searches of Americans’ communications obtained under Section 702. Even after an effort to shape up for the reauthorization debate, in 2022 the FBI still conducted more than 200,000 such warrantless searches. Now former intelligence community officials are waging a media campaign to scare Congress into submitting to a “clean” or mildly revised reauthorization of Section 702. Predictably, they are resorting to scare tactics to get their clean reauthorization. Rep. Andy Biggs, Chairman of the House Judiciary Subcommittee on Crime and Federal Government Surveillance, earlier this year warned: “The FBI and federal intelligence agencies use scare tactics to convince Congress that these unchecked powers are the only method available to protect our nation from harm. Well, every American should be scared to know federal agents are spying on them, even if they have nothing to hide.” Below is the first of our “Myths vs. Facts” responses from PPSA to fables being foisted by advocates of the intelligence community. Intelligence Community MYTH: A warrant requirement to search for Americans’ private data and communications in the Section 702 database would be “drastic and unwarranted,” putting the American homeland at risk. Congress must not let Section 702 expire. FACT: We can protect national security and have a foreign surveillance authority that respects the constitutional rights of American citizens. A warrant requirement is by definition not a proposal to let Section 702 expire at the end of this year. Indeed, Section 702 expiration can only happen if surveillance hawks fail to agree to significant reform. They cannot play a game of chicken and then act like Chicken Littles. If national security is being risked by the expiration of Section 702, then it will be the champions of the intelligence community who will cause it to happen. The specific intelligence community argument against warrants when Americans are surveilled makes no sense. The stated purpose of Section 702 is to conduct surveillance of foreign targets outside the United States. The government’s own Section 702 success stories all involve obtaining critical intelligence about plots by hostile foreign actors. It is wrong and patently absurd to sidestep Americans’ constitutional rights and warrantlessly surveil our own citizens in the name of foreign surveillance. Reform proposals, such as a warrant requirement for the surveillance of Americans’ communications, are not radical proposals. It is the ongoing mass surveillance of Americans who’ve done nothing remotely suspicious by our own government that is radical. The Fourth Amendment of the U.S. Constitution protects Americans against “unreasonable” searches and seizures. But what is unreasonable? Is a low-flying drone taking photos of you and your property behind a privacy fence reasonable?
In October, the Michigan Supreme Court will hear oral arguments in what could well become a landmark privacy case. The outcome may help determine the national limits of drone surveillance – and perhaps influence the limits of government surveillance – for all Americans. The facts are pretty simple. Todd and Heather Maxon of Long Lake Township in Michigan live on a five-acre estate, where Todd likes to repair old cars. In 2008, the Township government charged the Maxons with operating an illegal junkyard. The couple and the Township reached a settlement. In 2018, the Township received tips that the Maxons had violated their settlement by bringing more cars onto their property, even though such vehicles were not visible from the street. So the Township hired a private drone operator to fly a high-resolution camera over the Maxon property to take images. The Maxons sued, claiming that their Fourth Amendment rights were violated. A lower court agreed with the government but was overturned in 2021 by the Michigan Court of Appeals. That court ordered that the drone photos be suppressed. At the heart of this case is the “reasonable expectation of privacy” articulated by Supreme Court Justice John Marshall Harlan II in Katz v. United States (1967). But technology keeps testing what is a reasonable expectation of privacy. The Supreme Court has zigged and zagged along the way, once upholding a wiretap to be permissible because it occurred at the telephone pole and did not require a physical intrusion into the home. Katz overturned that standard, invalidating an FBI wiretap of a public payphone, where the caller (a sports bookie) had a reasonable expectation that he would not be overheard. “The Fourth Amendment protects people, not places,” Justice Potter Steward declared in the Court’s majority opinion. But the Court returned somewhat to the physical intrusion standard – invalidating thermal imaging by police from the street that penetrated inside a target’s home in Kyllo v. United States (2001). The Cato Institute and Rutherford Institute, in an amicus brief, noted the problem with the physical intrusion standard: “At present, police are free to go through people’s garbage, look into their barn with a flashlight, and read through their bank records without going through the hassle of first securing a warrant.” We now live in an age of ubiquitous digital intrusion with government purchases of our private data, as well as optical intrusion from drones and other aerial surveillance. In other words, the current privacy standard is a jumbled mess. That is why the Maxon case is potentially so important. At its simplest, it will determine if drones – an increasingly ubiquitous reality in American life – will be freely used to spy on Americans in their backyards (as the New York City Police recently did over backyard barbecues during Labor Day). But we think the Maxon case may prove to be pivotal in defining – perhaps, eventually, by the U.S. Supreme Court – what privacy and reasonableness mean in an era of drones, facial recognition software, and artificial intelligence. For years PPSA has documented the increasing disposition of federal intelligence and law enforcement agencies to use the ever-expanding Glomar response – a “cannot confirm or deny” answer once reserved for the nation’s most closely guarded secrets – as a blanket response to any meddlesome Freedom of Information Act (FOIA) requests.
We should not overlook, however, another handy tool for FOIA avoidance, and that is to release the requested document but redact many or all of its meaningful parts. Now the Department of Justice Office of the General Counsel has perfected this technique, taking it to its logical end. It began in 2020 when PPSA joined with Demand Progress to file a FOIA request. Our request concerned surveillance that may be taking place under no statute, but instead under a self-professed authority of the executive branch known as Executive Order 12333. The reply from the FBI is, in its own way, telling. In the DOJ response, a certain Mr. or Ms. BLANK who holds the title of BLANK in the Office of the General Counsel returned with 40 pages of responsive documents. Thirty-nine pages are redacted in their entirety, as is the 40th page, with the redacted name of the signator and his/her redacted title, but with one, unredacted statement: Hope that’s helpful. There’s honestly no other way to take this than the Department of Justice shooting a middle finger at the very idea of a FOIA request, an exercise of the Freedom of Information Act, passed by Congress and signed into law by President Lyndon Johnson. This is a shame because the subject of this request is an important one. Demand Progress and PPSA based our FOIA request on a July 2020 letter from now-retired Sen. Patrick Leahy (D-VT) and current Sen. Mike Lee (R-UT) to then-Attorney General William Barr and then-Director of National Intelligence John Ratcliffe. The two senators noted the expiration of Section 215 of the Foreign Intelligence Surveillance Act (FISA), commonly known as the “business records” provision of FISA. The intelligence community had vociferously lobbied for the renewal of Section 215 with predictions that allowing its expiration would lead to something akin to the city-destroying scenes in the 1996 movie Independence Day. Then the Trump Administration called their bluff and allowed this authority to expire. The response from the intelligence community? Crickets. The sudden complacency of the intelligence community struck many as suspicious. Were federal intelligence and law enforcement agencies shifting their surveillance to another authority? Sens. Leahy and Lee seemed to think so. They wrote: “At times the executive branch has tenuously relied on Executive Order 12333, issued in 1981, to conduct surveillance operations wholly independent of any statutory authorization … This would constitute a system of surveillance with no congressional oversight potentially resulting in programmatic Fourth Amendment violations at tremendous scale … We strongly believe that such reliance on Executive Order 12333 would be plainly illegal.” This July 2020 letter, with a detailed series of penetrating questions about the practice and scope of 12333 surveillance, was issued by two powerful and respected members of the United States Senate … And it hit the walls of the Department of Justice and the Office of the Director of National Intelligence with all the full force of wet spaghetti. As with so many other congressional requests, this letter was not answered in any substantive way. So Demand Progress joined with PPSA in October 2020, in an effort to use the law to compel an answer, this time as a formal FOIA request. We leveraged that law to request responsive documents that would reveal how the agencies might be repurposing EO 12333 to pick up the slack from the expired 215 authority, in order to spy on persons inside the United States. And this is the answer we get. It can only be taken, in a general way, as confirmation that Executive Order 12333 is, in fact, being relied upon for the surveillance of people in the United States. This is one more reason why Congress should use the reauthorization of Section 702 to seek broad surveillance reform, including significant guardrails on Executive Order 12333. With mounting evidence of abuses of Americans’ civil rights, a powerful coalition of leading conservatives and liberals in Congress is building steam to do just that. Hope that’s helpful. |
Categories
All
|






















 RSS Feed
RSS Feed