|
In response to a Freedom of Information Act request filed by PPSA, the Bureau of Alcohol, Tobacco, Firearms and Explosives (ATF) responded with a batch of documents, including internal training material. In those documents, the ATF confirmed that it uses cell site simulators, commonly known as “stingrays,” to track Americans.
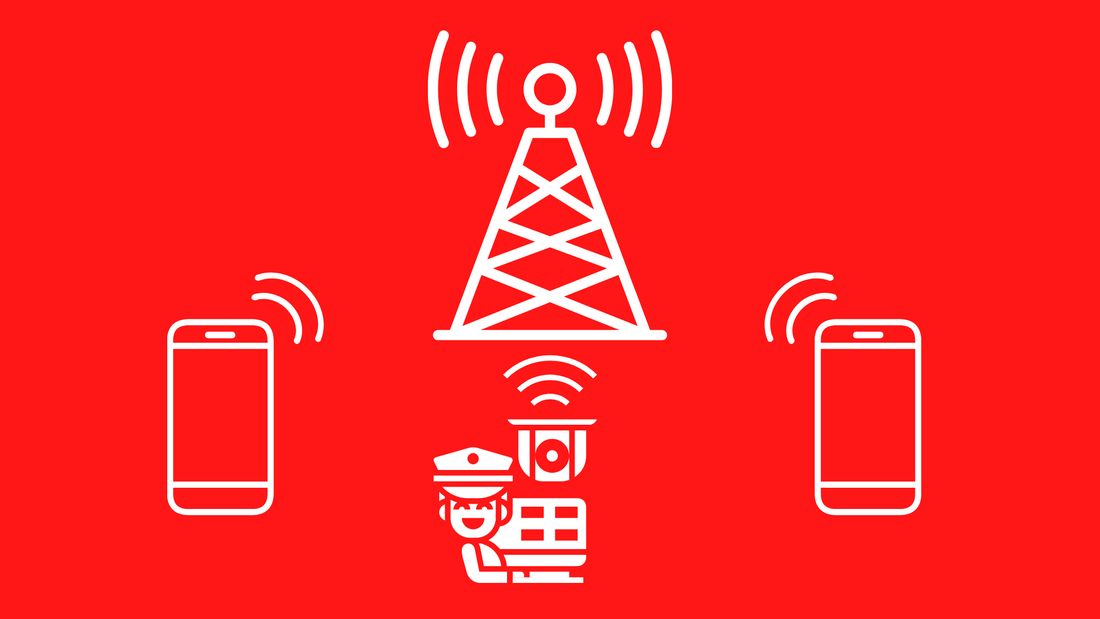
Stingrays impersonate cell towers to track mobile device users. These devices give the government the ability to conduct sweeping dragnets of the metadata, location, text messages, and other data stored by the cell phones of people within a geofenced area. Through stingrays, the government can obtain a disturbing amount of information. The ATF has gone to great lengths to obfuscate their usage of stingrays, despite one official document claiming stingrays are “used on almost a daily basis in the field.” The ATF stressed that stingrays are not precise location trackers like GPS, despite the plethora of information stingrays can still provide. Answers to questions from the Senate Appropriations Committee about the ATF’s usage of stingrays and license plate reader technology are entirely blacked out in the ATF documents we received. An ATF policy conceals the use of these devices from their targets, even when relevant to their legal defense. Example: When an ATF agent interviewed by a defense attorney revealed the use of the equipment, a large group email was sent out saying: "This was obviously a mistake and is being handled." The information released by the ATF confirms the agency is indeed utilizing stingray technology. Although the agency attempted to minimize usage the usage of stingrays, it is clear they are being widely used against Americans. PPSA will continue to track stingray usage and report forthcoming responses to pending Freedom of Information Act requests with federal agencies. Comments are closed.
|
Categories
All
|

 RSS Feed
RSS Feed